Nearly 4 billion(nové okno) phishing emails are sent across the world every day, making it the most common form of cybercrime today. With this many phishing emails out in the web, the likelihood of accidentally clicking an unsafe link or falling for a phishing scheme isn’t as uncommon as you might think — even if you’re good at spotting fake emails.
Cybersecurity attacks like phishing have evolved from obvious scams to highly sophisticated ones, using friendly banter and eerily familiar personalization in the hopes that you let your guard down just long enough to reveal sensitive information.
But this doesn’t mean you’re destined to fall for a phishing scam. It’s more important than ever to know how to detect a phishing attack, and routine training and education on phishing email examples can help keep you vigilant and ahead of the cybercrime curve.
In this article, we’ve included three phishing attack examples that could end up in your inbox. First, ask yourself if you would have spotted them as fake, then learn how to protect yourself and your data using Proton’s end-to-end encrypted services.
How does phishing work?
Phishing scams are designed to trick you into revealing personal information by posing as a trusted source. Instead of attempting to hack your computer or software, cybercriminals now focus on tricking you with your own public information. It’s a common tactic for hackers to sift through the internet for data from public social media profiles and online records to make their phishing attempts even more believable.
By spoofing emails from trusted sources, hackers can coax you into revealing your login credentials, bank details, or even your Social Security number. Scammers impersonate legitimate entities like banks, online retailers, and even government agencies to trick you into sharing sensitive information by creating a false sense of fear or urgency.
A Phishing email might claim that your account has been compromised, your password needs resetting, or a suspicious high-value transaction has occurred. They’ll typically ask you to respond immediately by clicking on a malicious link or confirming sensitive information, like your login credentials or credit card number.
You may then be redirected to the actual service website or receive a message thanking you for taking action. Unfortunately, the scammer now has access to your device or whatever information you shared.
No matter the situation, if you fall for a phishing scam, your personal data and identity can be stolen, your device can become infected with malware, or you can be tricked into giving a criminal money via ransomware.
First potential phishing attack
Imagine you open your inbox and you see the following three emails. At first glance, would you think they were legitimate or that they were phishing attacks?
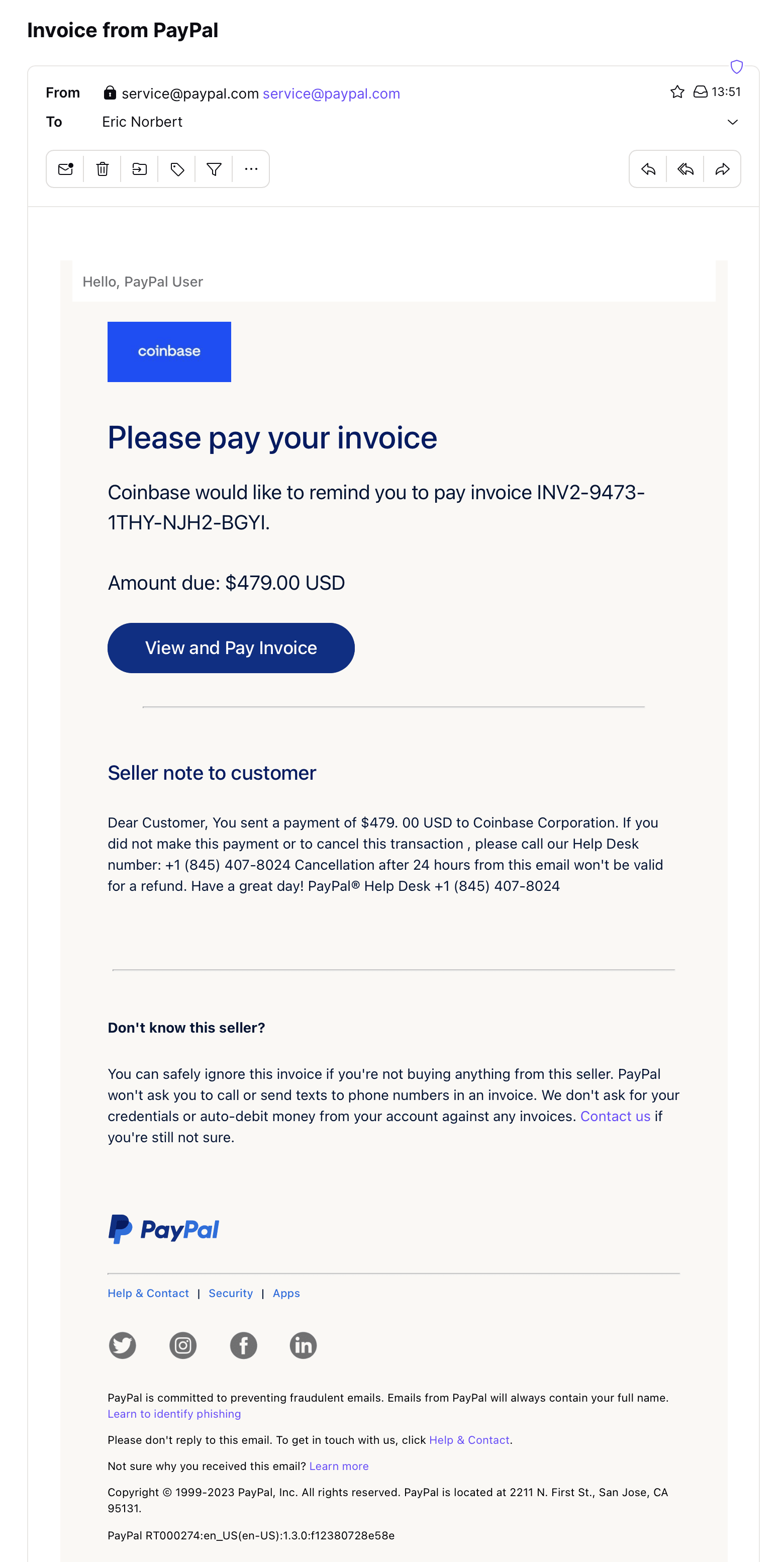
If you said this is a phishing attack, you’re correct. It’s a new devious type of phishing attack that uses a legitimate domain (in this case, from PayPal) to send fake invoices. By abusing legitimate email domains, these phishing attacks are more likely to be viewed as legitimate by email services and the people being targeted.
In February of 2023 alone, we detected over 15,000 phishing emails sent using these techniques.
The attackers hope you’ll call the phone number listed in the email to contest or cancel the charge. But this number does not belong to PayPal. Instead of calling PayPal’s customer support, you’re actually calling the attacker, who is pretending to be customer support.
Typically, they’ll then inform you that you’ve been hacked and ask you to download a remote administration tool to your computer so they can fix the problem for you. If you fall for the ruse and download the program they send, you’ll actually give the attacker direct access to your device, allowing them to launch even more attacks.
Second potential phishing attack
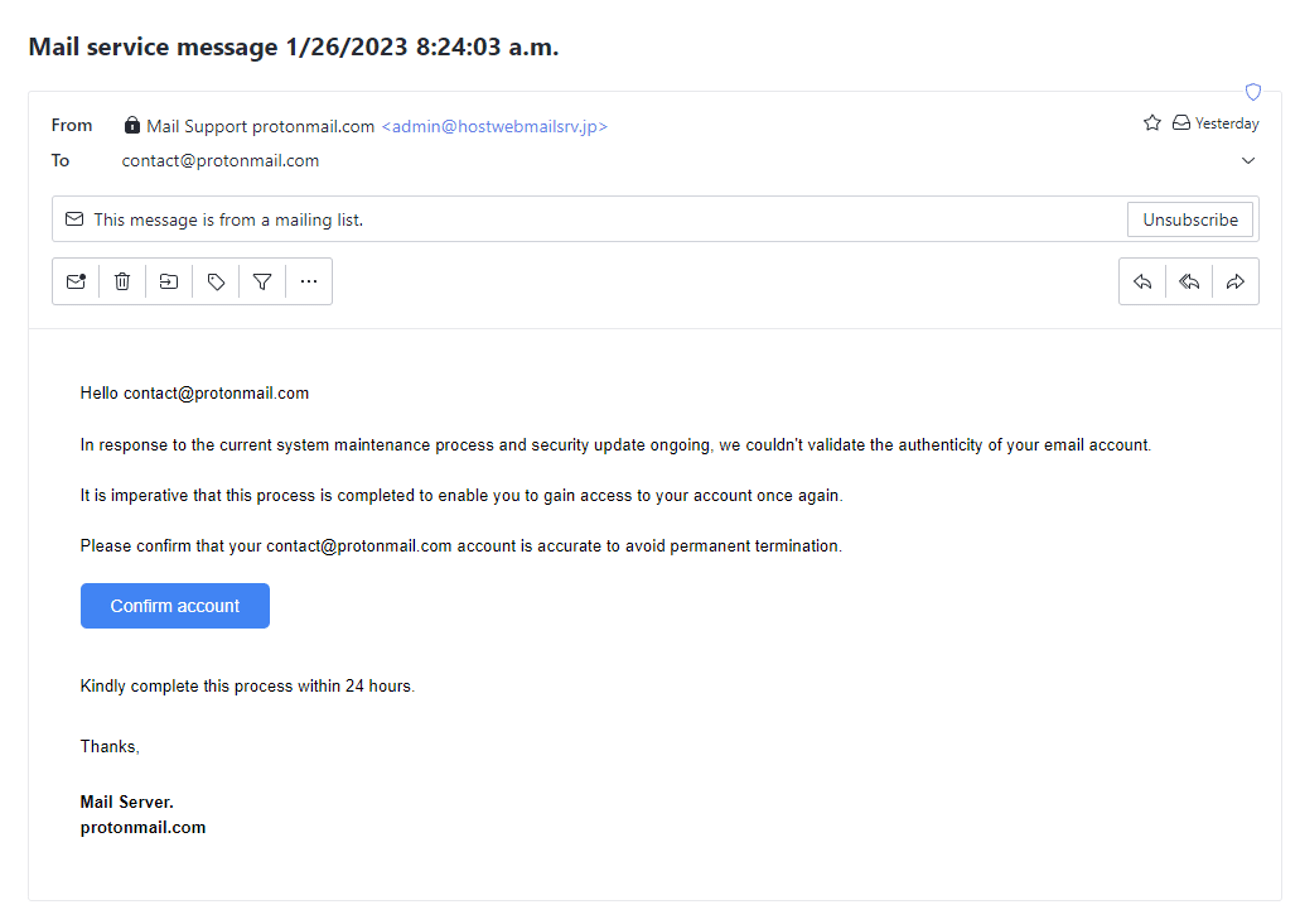
If you said this was a phishing attack, you’re correct. Attackers often attempt to impersonate Proton Mail knowing that people trust us to protect their personal information. The first clue is the From field. While this email claims to be from Mail Support protonmail.com, but if you look at the email that follows, it doesn’t use a recognized Proton Mail domain (this one uses an @hostwebmailsrv.jp domain). It also doesn’t have our Official badge, which is how we verify legitimate Proton Mail emails.
This is also a classic phishing attack in that it tries to instill a sense of urgency in you by saying you must confirm your account or it will be permanently terminated.
Third potential phishing attack
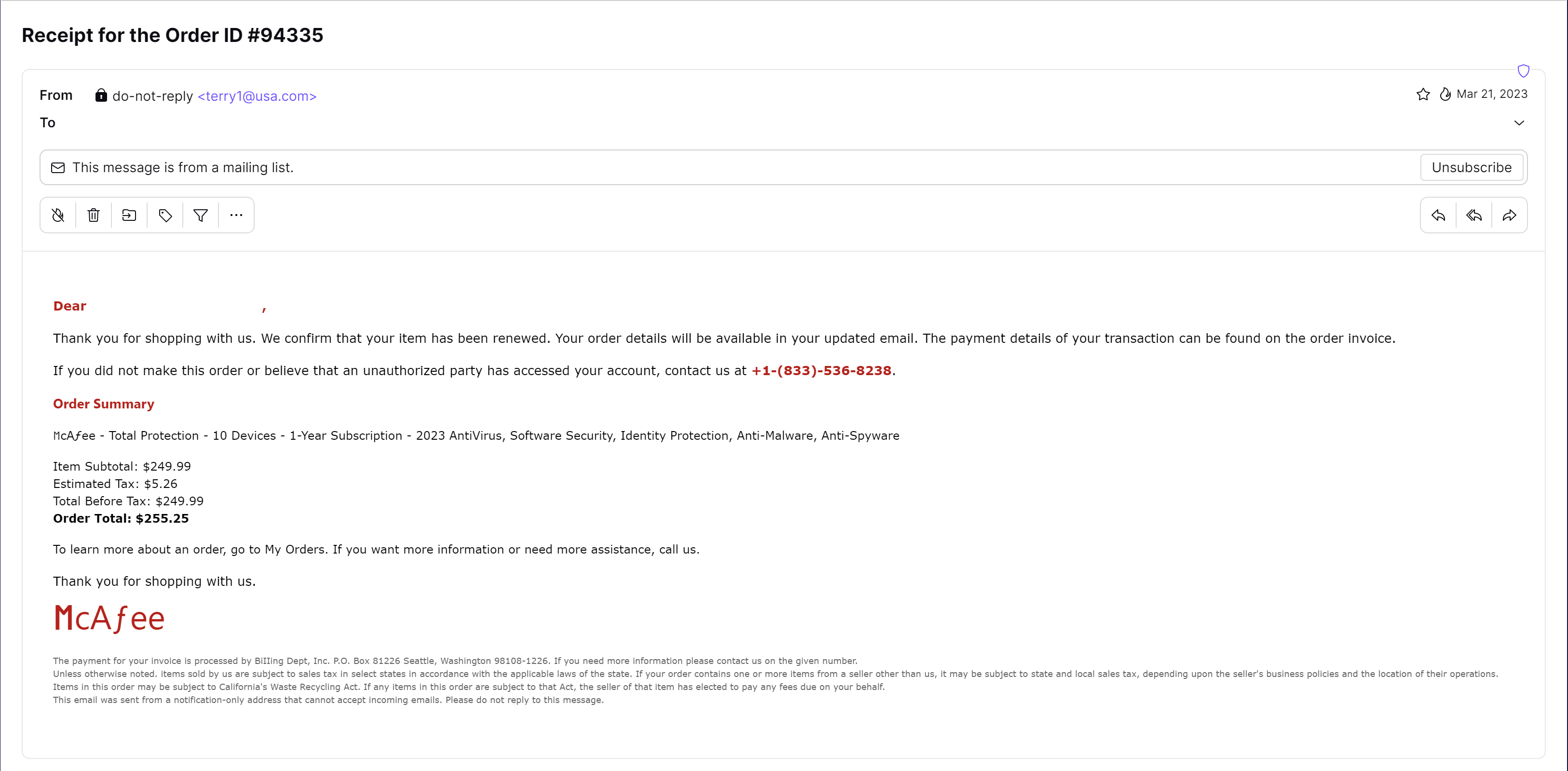
If you said this was a phishing attack, you’re correct. This example contains plenty of red flags, such as the email address in the From field (it’s unlikely McAfee would use an @usa.com domain) and the clearly incorrect McAfee logo at the bottom.
This is a less sophisticated version of the PayPal attack, hoping to fool you into calling the given phone number so someone can convince you to hand over your account details.
How to protect yourself from phishing scams
- Look for red flags: Be skeptical of unsolicited emails, especially those with urgent or overly dramatic language. Check the sender’s email address, the URL links, and any attachments for signs of fraud.
- Enable two-factor authentication (2FA): Enabling 2FA for all your accounts adds an extra layer of security. If a scammer gets your password, they still won’t be able to access your account without the second layer of authentication (usually a code sent to your personal phone or email that will also alert you to the suspicious activity).
- Keep your software updated: Your operating system, browsers, and antivirus software should be updated frequently to protect against new phishing tactics and malware.
- Verify before you click: If you receive a suspicious email, don’t click any links. Instead, contact the company directly using the contact information from their official website — not the contact information included in the email (which could just lead back to the scammer).
Use Proton Mail to find and block phishing emails
Maintaining this level of caution can be exhausting, especially when you have to deal with dozens of legitimate emails every day. Thankfully, Proton Mail makes this job easier.
We block over 130,000 phishing attacks every day, and we’re constantly on the lookout for new strategies attackers use to avoid detection. With Proton, we give you the tools to make educated decisions when faced with suspicious emails.
Block scammers with PhishGuard
Proton Mail’s PhishGuard stops most phishing attempts before they ever reach your inbox. PhishGuard authenticates emails using DMARC, DKIM, and SPF checks. If an email fails authentication, Proton Mail will block it or notify you so you know which emails to examine more closely — like the phishing attempt in example two.
Identify suspicious links with link confirmation
Attackers can hide malicious links in emails that may redirect you to another URL. Proton Mail’s link confirmation displays the actual URL you are being redirected to, allowing you to detect suspicious links hidden behind innocuous-looking text.

Use aliases to protect yourself against data breaches and phishing attempts
With email aliases, you can associate an alias with a specific service, allowing you to segment your contacts and detect imposters.
Imagine you sign up for a website using an alias (website1@yourname.simplelogin.com) and then that website sends an email to your real email address (realemail@protonmail.com). In this case, you can assume it’s likely not a legitimate email, as the actual website didn’t have access to your real email address when you signed up.
Avoid malicious websites with NetShield Ad-blocker
If you have a paid plan for Proton VPN, you can turn on NetShield Ad-blocker(nové okno), which will prevent you from accessing sites that are known to be dangerous.
Protect your account with physical security keys
Even if you fall victim to a phishing attack, you can protect your accounts by adding extra layers of security to your online accounts. With two-factor authentication (2FA), especially 2FA using hardware security keys like Yubikeys, you can physically verify that you are the account owner. This means that even if an attacker steals your login credentials, they cannot gain control of the account without the physical key associated with it.
Prevent attackers from accessing your Proton Account
Even if you accidentally compromise your Proton Account by falling for a phishing attack, you can still keep your data safe. Proton has automated account security protection that suspends accounts before attackers can get in. We also send login alerts for each login attempt.
If you see a login alert that you didn’t trigger, you can always log out of all unauthorized sessions and change your password.
Stay safe with Proton
As phishing attacks become more sophisticated, it’s important to protect your data, and that starts with choosing a secure email, like Proton Mail. Additionally, staying informed about the latest tactics is key to protecting yourself from cybersecurity attacks. For more tips on how to avoid phishing scams, check out our guides on other popular phishing tactics like quishing.
You can minimize the risk of falling victim to these malicious attacks by staying vigilant and using proactive security services like Proton, which was created by privacy-focused scientists with your security in mind.
Don’t let scammers outsmart you. Start using Proton Mail today and keep your personal information safe from attacks around the clock.





